There’s a growing demand for skilled cybersecurity specialists who can adapt quickly to a rapidly changing technical landscape. That said, you still need a powerful resume to generate interviews in today’s competitive job market. Whether you’re a seasoned cybersecurity analyst or a recent graduate entering the field for the first time, we’ll provide expert tips and insights to help you succeed during the job search.
Regardless of your years of experience, your resume should communicate your strengths clearly and fast. Hiring managers often spend seconds scanning resumes, so it’s critical to emphasize your technical expertise, security tools, and accomplishments early. This guide will help you build a cybersecurity resume that’s focused, professional, and aligned with your career goals.
Cybersecurity professionals have a uniquely high-stakes role. You’re not just monitoring alerts, but you’re preventing data breaches, protecting intellectual property, ensuring regulatory compliance, and managing risk in real time. The best cybersecurity resumes highlight both proactive strategy and technical execution.
Key takeaways:
- Emphasize your specializations: Provide tangible examples of your cybersecurity expertise in key areas such as incident response, AI security, threat detection, and network security.
- Quantify your accomplishments: Incorporate hard numbers, data, and metrics to demonstrate the impact you’ve had on cybersecurity policies and procedures. For example, you might highlight your track record of reducing incident response times. ,
- Use keywords for ATS: Feature keywords and skills from the job description to get your resume past the applicant tracking system (ATS), such as SIEM tools, penetration testing, risk mitigation, and vulnerability management.
Most Popular Cybersecurity Resumes
Cybersecurity Analyst Resume Example

Why This Resume Is a Great Example
Taylor’s resume offers a strong mix of quantifiable accomplishments and relevant security expertise. The profile immediately communicates their technical specialties and aligns with common employer needs in cybersecurity. Each job includes metrics that reflect real-world impact — like reducing false positives by 38% or contributing to ISO 27001 certification. The formatting keeps the most important details up top, while the skills section and certifications add depth and credibility.
Key Tip: When your skills directly map to industry certifications and tools in the job description, you’re more likely to get past ATS filters.
Entry-Level Cybersecurity Resume Example

Why This Resume Is a Great Example
Alex’s resume shows how new graduates can stand out by highlighting internships, academic projects, and relevant certifications. The profile sets the tone with a focus on curiosity and technical readiness, while the experience section provides concrete examples of hands-on contributions, even in support roles.
Key Tip: If you’re early in your career, combine work-study roles, lab projects, and internships to show initiative. Learn how to build a strong entry-level resume.
Cybersecurity Intern Resume Example

Why This Resume Is a Great Example
Jordan’s resume demonstrates the value of blending academic and internship experience. Even without full-time roles, Jordan highlights accomplishments that reflect initiative, like presenting project results and contributing to live network assessments.
Key Tip: Use university research and lab experience as evidence of technical skill. Learn how to highlight early-career strengths.
Cybersecurity Executive Resume Example
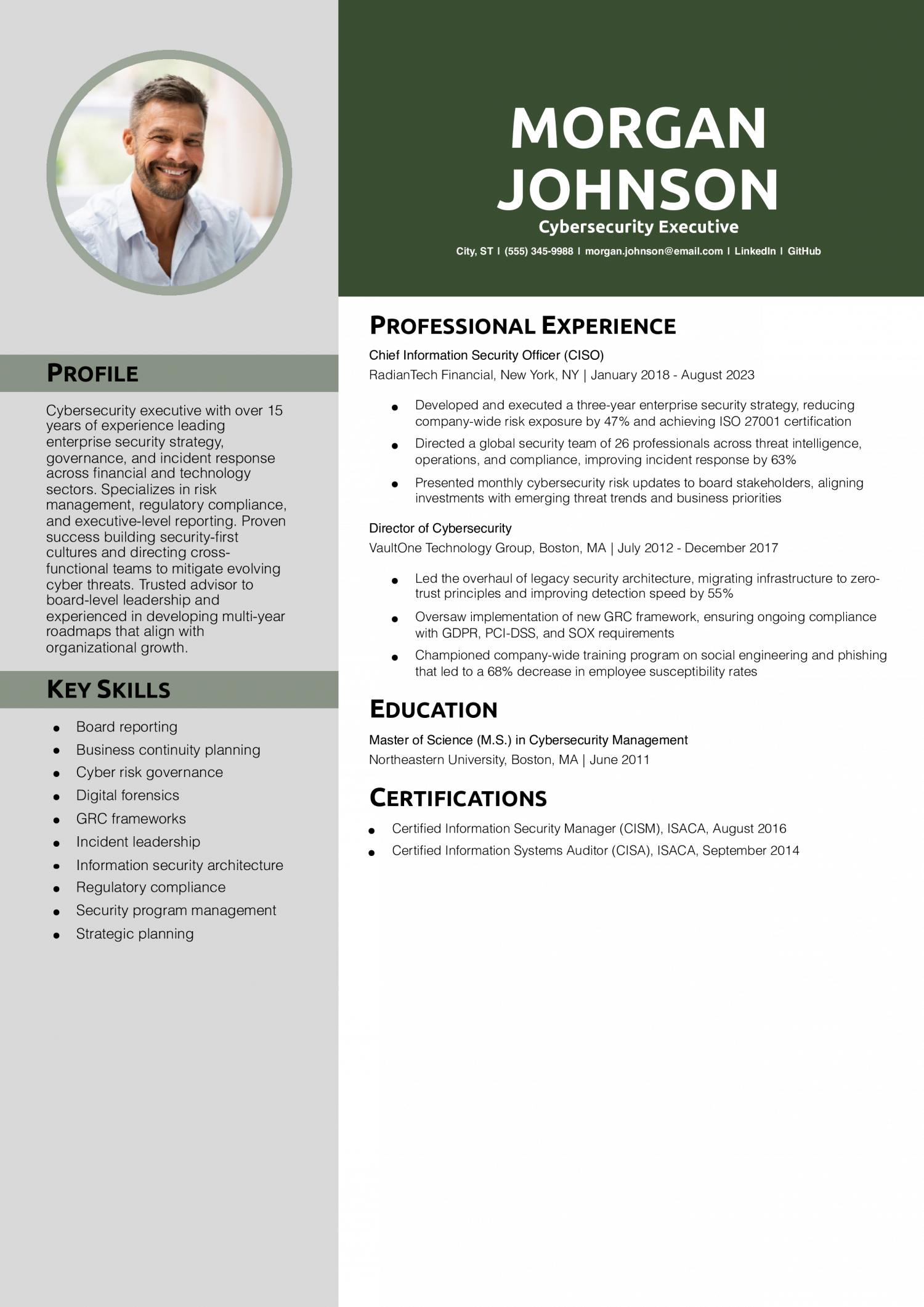
Why This Resume Is a Great Example
Morgan’s resume stands out with its executive-level focus. The profile positions them as a strategic leader, while the bullets show measured results in governance, team leadership, and enterprise-wide transformation.
Key Tip: At the executive level, focus on impact, not task lists. Show how your leadership drove outcomes. Read more about matching resume content to senior roles.
Cybersecurity Consultant Resume Example

Why This Resume Is a Great Example
Casey’s resume highlights their consulting background with results from multiple client engagements, showing how they drive improvement across varied industries. The focus on client outcomes and compliance strengthens their credibility as a trusted security advisor.
Key Tip: When applying for consulting roles, demonstrate versatility by showcasing success across industries. Learn how to position cross-industry work.
Cybersecurity Engineer Resume Example

Why This Resume Is a Great Example
Jamie’s resume is strong because it focuses on engineering impact — not just tools, but outcomes. Phrases like “reduced breach attempts by 64%” and “decreased triage time by 70%” quantify the value of automation and infrastructure upgrades.
Key Tip: Engineers should balance technical tools with outcome-driven storytelling. Learn more about highlighting technical skills in your IT resume.
Cloud Security Analyst Resume Example

Why This Resume Is a Great Example
Cameron’s resume demonstrates specialization in cloud security, which is in high demand. The experience section directly references tools and platforms (like Jenkins and S3) while showing business impact through metrics.
Key Tip: Be specific about platforms and certifications when applying for cloud roles. See how to showcase cloud experience.
Cybersecurity Risk Analyst Resume Example

Why This Resume Is a Great Example
Drew’s resume effectively blends technical knowledge and business strategy. The use of frameworks like FAIR and NIST helps establish credibility, while clear metrics show how their work drives better decision-making.
Key Tip: Tailor risk roles with the language of frameworks and metrics. Get help choosing the best resume format.
Penetration Tester Resume Example

Why This Resume Is a Great Example
Riley’s resume showcases deep technical fluency and emphasizes real-world results, like exploit success and reduction in security risks. Specific tools, metrics, and methodology create credibility for a hands-on offensive security role.
Key Tip: Use real numbers and well-known tools to prove credibility in penetration testing. Read more on how to show off security skills.
Security Operations Center (SOC) Analyst Resume Example

Why This Resume Is a Great Example
Pat’s resume stands out because it emphasizes speed, accuracy, and value in a fast-paced SOC environment. Tying metrics like “98% incident accuracy rate” and “triage time from 15 to 7 minutes” demonstrates clear performance and growth.
Key Tip: Metrics matter most in high-volume roles — don’t just say you handled incidents, show how well you did it. Get more tips on sharing work experience.
Application Security Analyst Resume Example

Why This Resume Is a Great Example
Taylor’s resume blends development knowledge with a strong focus on secure coding. It shows not only testing tools and tasks but also the impact of training, collaboration, and prevention strategies.
Key Tip: Application security requires communication — if you’ve led workshops or supported developers, highlight it. Learn more about writing a convincing resume profile.
Cybersecurity Compliance Analyst Resume Example

Why This Resume Is a Great Example
Alex’s resume succeeds by clearly aligning compliance responsibilities with regulatory frameworks. From internal audits to dashboard tracking, every task supports traceable security improvements.
Key Tip: When applying for GRC roles, naming the frameworks you’ve worked with is essential. Learn how to list your work experience.
Threat Intelligence Analyst Resume Example

Why This Resume Is a Great Example
Jordan’s resume clearly defines their specialty in threat intelligence, and each bullet point ties to action that supports detection or strategy. Tools, frameworks, and outcomes are front and center.
Key Tip: For threat intelligence roles, link your work to decision-making. Find out how to build more strategic resumes.
Identity and Access Management (IAM) Analyst Resume Example
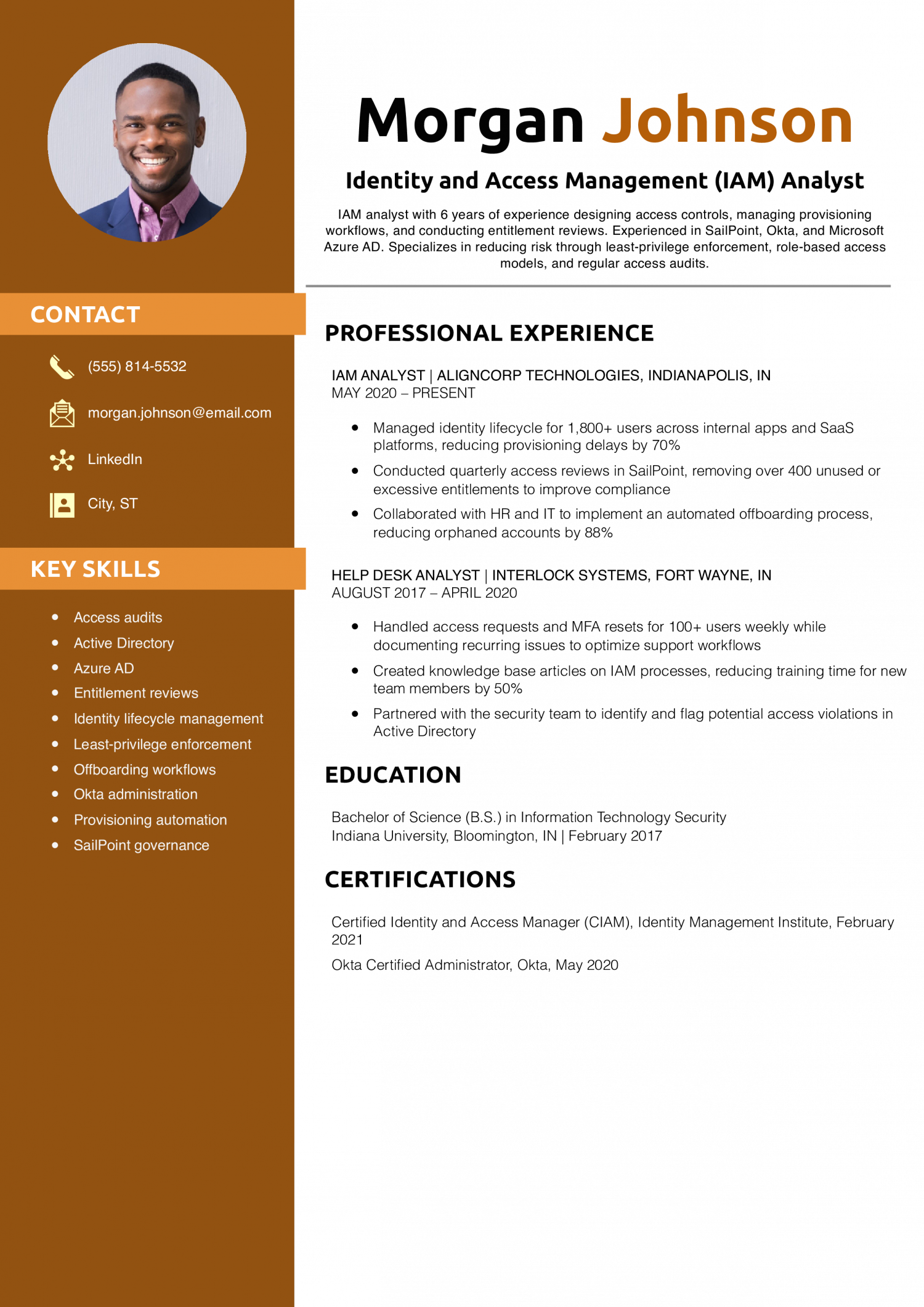
Why This Resume Is a Great Example
Morgan’s resume showcases IAM responsibilities with a focus on business impact, like reducing provisioning delays and automating offboarding. It communicates both tools and results clearly.
Key Tip: IAM roles often involve coordination — show how your work reduced risk or improved onboarding. See how to build a professional resume.
Cybersecurity Project Manager Resume Example

Why This Resume Is a Great Example
Casey’s resume captures the impact of leadership through metrics like project completion rates and stakeholder satisfaction. The bullets demonstrate control over scope, team dynamics, and business outcomes.
Key Tip: Show how you manage risk and value delivery at the same time. Learn how to update your resume for balance.
Cybersecurity Trainer Resume Example

Why This Resume Is a Great Example
Jamie’s resume demonstrates subject matter mastery and the ability to influence behavior. The results — like lowered phishing rates and boosted course completions — show tangible outcomes.
Key Tip: If you’re in a training or education role, always highlight engagement and behavior change. Learn how to spotlight skills.
Information Security Specialist Resume Example
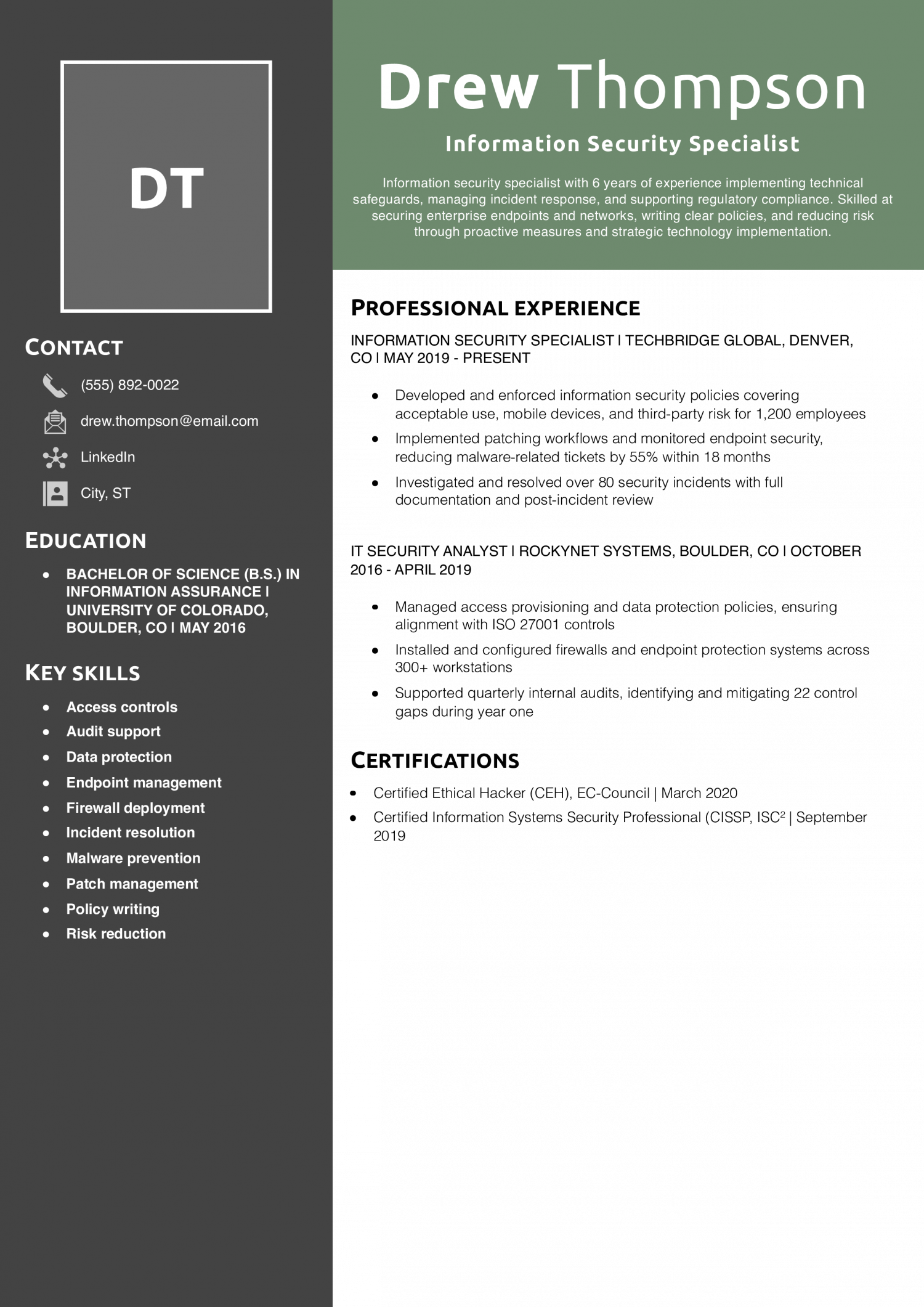
Why This Resume Is a Great Example
Drew’s resume does a great job showing long-term risk reduction through system hardening and process improvements. The clear metrics show that the work made a difference.
Key Tip: When describing “responsible for” tasks, rephrase to emphasize outcomes and measurements. See what to say instead of responsible.
Industrial Control Systems (ICS) Security Analyst Resume Example

Why This Resume Is a Great Example
Cameron’s resume zeroes in on a specialized and high-demand field. The use of specific protocols and tools (like Nozomi and Modbus) proves technical fluency in a niche environment.
Key Tip: Niche roles benefit from niche language — show what’s unique to your field. Read more on how to present job titles.
Digital Forensics Analyst Resume Example

Why This Resume Is a Great Example
Riley’s resume aligns forensic skills with both legal and investigative outcomes, a crucial trait for this field. Real-world case numbers and tool names increase credibility.
Key Tip: Forensics work often supports legal proceedings — emphasize documentation, reporting, and compliance. Learn how to list publications on your resume.
Cybersecurity Text-Only Resume Examples and Templates
How To Write a Cybersecurity Resume Example
Before crafting your content, it’s important to select a professional template that allows you to structure your information effectively. Opt for a straightforward layout with clearly delineated sections that allows the hiring manager to easily navigate your qualifications and achievements. Your resume template should always include these sections:
- Contact information
- Profile
- Key skills
- Professional experience
- Education and certifications
1. Share your contact information
Include your full name, phone number, professional email address, location, and links to your LinkedIn or GitHub profile. Carefully review the accuracy of your information to ensure potential employers can reach out to schedule you for an interview.
Example:
JORDAN RIVERA
[email protected] | (555) 123-4567 | Seattle, WA | linkedin.com/in/jordanriveracyber | github.com/jordansec
2. Write a compelling profile summarizing your cybersecurity qualifications
Lead with an engaging opening summary to draw the reader in and entice them to read further. Start with a sentence that lists your title, years of experience, and three to four specializations that match the job description. Provide a compelling overview of your career and highlight your most impressive achievements within the cybersecurity field. This immediately shows potential employers that you have the knowledge and expertise to help their organizations enhance security protocols and mitigate evolving cyber threats.
Senior-level profile example
Cybersecurity analyst with over 10 years of experience in enterprise network security, vulnerability management, and compliance auditing. Proven success leading incident response and reducing organizational risk exposure using SIEM tools and penetration testing.
Entry-level profile example
Cybersecurity specialist with 2 years of experience supporting security operations, incident handling, and endpoint monitoring. Strong foundation in firewalls, access controls, and malware detection built through academic projects and internships.
3. Add an accomplishment-driven professional experience section
The strength of your work history will always be a pivotal factor during the hiring process. Companies aren’t interested in mundane job responsibilities; they want to see tangible examples of what you’ve accomplished during your career as a cybersecurity specialist. Take time to reflect on how you enhanced security processes, prevented threats, and reduced critical vulnerabilities. Craft concise yet impactful bullet points that demonstrate the value you can bring to potential employers.
Senior-level professional experience example
Lead cybersecurity analyst, TechCore Solutions, Austin, TX | February 2017 to present
- Reduced critical vulnerabilities by 70% through comprehensive quarterly assessments and implementation of patch management workflows
- Oversaw SOC operations, analyzing threat intelligence and coordinating incident response for a 24/7 enterprise security team
- Integrated Splunk SIEM to streamline log analysis and reduce detection time for threats by 60%
Entry-level professional experience example
Security operations center (SOC) analyst, NovaBank, Chicago, IL | June 2022 to present
- Triaged 200+ security events daily, escalating incidents according to response protocols
- Collaborated with engineering team to improve endpoint detection rules, leading to a 30% increase in early malware detection
- Performed vulnerability scans and assisted with remediation tracking using Tenable and Jira
Resume writer’s tip: Quantify your experience
Quantifying your accomplishments is a great way to establish a sense of scope for the hiring manager and enhance the impact of your bullet points. For example, say you developed and implemented new cybersecurity processes. You might emphasize how these procedures reduced vulnerabilities or improved incident response times by 30%.
Do
- “Blocked 95% of phishing attempts by implementing email filtering rules and conducting employee training sessions”
Don’t
- “Trained staff on phishing attacks”
Resume writer’s tip: Tailor your resume for each job type
To give yourself a competitive advantage during the job hunt, customize your resume towards a job type. Review multiple job descriptions for a job type and incorporate keywords and skills that align with that job type. For example, if a job description mentions identity and access management (IAM), emphasize your experience managing user authentication procedures to lower the risk of cyber threats.
What if you don’t have experience?
Even without hands-on experience, you can still build a compelling resume to position yourself for entry-level job opportunities. Rather than prioritizing work history, focus on your internships, academic projects, and independent projects to show hiring managers that you have the technical acumen and knowledge to succeed in the position.
4. Include relevant education and certifications
Although your professional experience will always carry more weight, it’s important to highlight your education and certifications prominently. A bachelor’s degree in computer science, information technology, or cybersecurity is typically a minimum requirement for these types of positions. You should also consider obtaining other industry credentials to further establish your credibility, such as a Certified Information Systems Security Professional (CISSP) certification.
Education
Template:
[Degree Name and Major]
[School Name] | [City, ST]
Example:
Bachelor of Science (B.S.) in Cybersecurity
Drexel University | Philadelphia, PA
Certifications
Template:
[Certification Name] | [Awarding Organization] | [Completion Date]
Example:
CompTIA Security+ | CompTIA | June 2023
Certified Information Systems Security Professional (CISSP) | ISC² | January 2024
GIAC Security Essentials Certification (GSEC) | GIAC | March 2022
5. List pertinent key skills
To ensure compliance with applicant tracking systems (ATS), you need a robust skills section that includes keywords directly from the job posting. In addition to technical proficiencies such as cloud security, identity and access management, and penetration testing, be sure to include a number of interpersonal skills. This shows potential employers that you can provide cybersecurity training and collaborate effectively in fast-paced, cross-functional team environments.
| Key skills | |
|---|---|
| Access control systems | Cloud security |
| Compliance auditing | Endpoint detection and response (EDR) |
| Firewall configuration | Identity and access management (IAM) |
| Incident response | Intrusion detection systems (IDS) |
| Malware analysis | Network forensics |
| NIST cybersecurity framework | Penetration testing |
| Risk assessment | Security awareness training |
| Security information and event management (SIEM) | Security operations center (SOC) procedures |
| Threat intelligence | Vulnerability scanning |
| Web application security | Zero Trust architecture |
Resume writer’s tip: Use common action verbs
Incorporating powerful action verbs is a great way to add an engaging element to your bullet points. Proactive language allows the hiring manager to visualize your contributions. Conversely, passive verbiage such as “responsible for,” and “assisted,” lessens the impact of your achievements and places you in much more of a supporting role. Below, you’ll find a list of action verbs you can use to craft your work history section:
| Action verbs | |
|---|---|
| Analyzed | Audited |
| Conducted | Collaborated |
| Created | Detected |
| Developed | Drove |
| Enhanced | Identified |
| Implemented | Improved |
| Investigated | Led |
| Managed | Mitigated |
| Monitored | Oversaw |
| Performed | Secured |
| Tested | Trained |
How To Pick the Best Cybersecurity Resume Template
Choose a resume template that highlights clarity, not clutter. A clean format ensures that ATS can read your content and that hiring managers focus on your skills and experience. Avoid heavy graphics, images, or columns that may confuse parsing software. Stick to consistent section headers and avoid overly stylized fonts.
Frequently Asked Questions: Cybersecurity Resume Examples and Advice
According to the Bureau of Labor Statistics, information security occupations are expected to grow by 28% over the next decade. While demand for cybersecurity specialists is increasing, the most lucrative opportunities will always invite the strongest competition. To stand out during the hiring process, it's essential to align your resume with the job description.
For instance, if a company is looking for a cybersecurity professional with a strong background in ISO27001 and NIST Cybersecurity Framework. In addition to listing these skills, emphasize your experience performing comprehensive audits to ensure compliance with these cybersecurity standards.
A reverse chronological format is ideal for most cybersecurity roles. This format places your most recent and relevant experience first, giving hiring managers a clear picture of your career progression. Entry-level candidates and recent graduates should consider using a combination approach that prioritizes your academic projects, certifications, and skills to help compensate for a limited work history.
Include a cover letter with your resume
Although cover letters aren’t always required for a cybersecurity job application, including one can help set you apart from other candidates. A customized cover letter allows you to address the employer directly, emphasizing why you’re the ideal fit for the organization’s culture. You can almost mention specific details about the company’s reputation, mission, or products and why this draws you to apply for the opportunity.
Check Out Related Examples
Resume Templates offers HR approved resume templates to help you create a professional resume in minutes. Choose from several template options and even pre-populate a resume from your profile.